Center for Networked Configurable Command, Control and Communications
Research
The Center of Excellence will address a number of fundamental research questions in the development of a robust, resilient, secure, and Fully Networked Command, Control and Communications infrastructure. The Center will focus on research that allows systems and sub-systems for sensing, data analysis, communications and networking, to be seamlessly integrated and adaptive to novel mission needs.
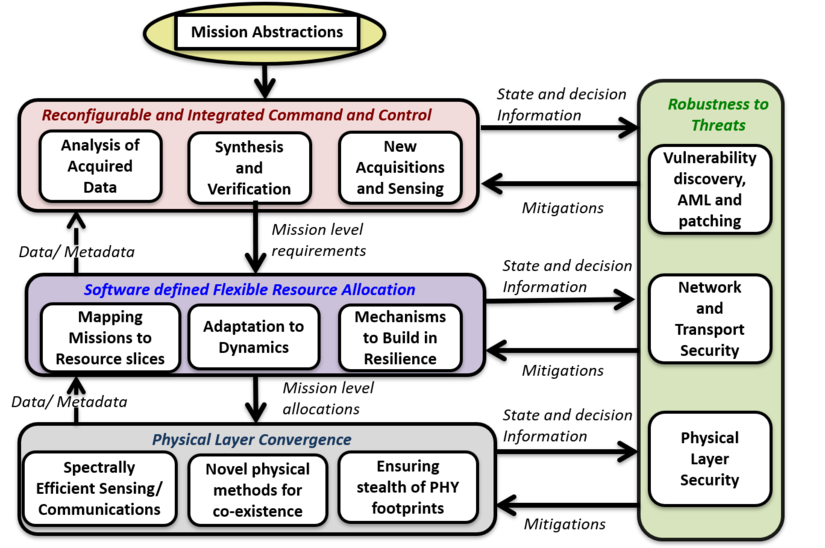
The CoE research is organized into four inter-dependent thrusts. The following figure shows the inter-relationships between the thrusts:
Thrust 1: Reconfigurable Framework for Integrated Command and Control, which will develop a new software plane and functional architecture, guided by robust machine learning (ML) models, to assess dynamic mission requirements, available resources, and environmental factors.
Thrust 2: Software Defined Flexible and Dynamic Network Resource Allocation and Resilience, which focuses on flexible division of available communication and computing resources into slices and can dynamically allocate these slices to the plurality of missions.
Thrust 3: Physical Layer Convergence of Sensing and Communications, whose goal is to maximize the utilization of the resources that are made available to the mission, via appropriate physical layer division and invocation of different physical modes.
Thrust 4: Robustness to Adversarial Disruptions on Sensing and Communications Infrastructure, which aims to provide robustness to adversarial attacks and fault resilience on all of the above.
The thrust-specific pages contain overviews of each thrust: Thrust 1 | Thrust 2 | Thrust 3 | Thrust 4
Publications can be found here.
Year 1 Accomplishments
Thrust 1 accomplishments include development of a distributed learning framework with uncertain data and resource constraints, that accounts for available resources (computation, bandwidth) and noise in data. Additionally, work was done on developing verification approaches for assessing application requirements on bandwidth, which will be applied to drive robust and flexible resource allocation.
Within Thrust 2, a preliminary design for a framework to reduce the computational overhead on edge devices while rapidly producing desired data has been completed, with implementation in progress. The framework is designed to achieve efficient adaptability to support dynamic data and resource fluctuation. Also, various SDN-based execution environments have been evaluated and analyzed to support agile ramp up of computational resources. An initial design of an agile computational environment with network function virtualization was completed.
In Thrust 3, a programmable massive MIMO millimeter-wave platform was developed. Novel research was performed on spectrum sharing for federated learning. Finally, two methods of waveform sharing between radar sensing and communications were designed and realized on hardware.
For Thrust 4, a novel method to thwart potent full-duplex jammers and eavesdroppers was developed. A new method to boost TCP performance of critical applications under resource duress was designed and implemented. Additionally, an investigation was performed on TCP impact during link switching between RF and millimeter wave links, and undergraduate project studied multi-path TCP. Finally, adversarial attacks on ML-based joint source-channel coding were studied, and initial work was performed on secret key establishment using full-duplex communications.
Year 2 Accomplishments
Thrust 1 accomplishments included studies on knowledge distillation for low-weight ML models in distributed learning and ansupervised distributed inference and learning with dynamic data. Also, implementation progressed on an experimental software platform for bounding and verifying resource usage of application code. Finally, fundamental modeling and algorithms were developed to perform threat detection for heterogeneous networks using online data.
Within Thrust 2, a preliminary formulation was developed of new data driven algorithms for resource allocation. Algorithms were developed for dynamic resource management in software-defined virtual networks. An agile virtualized computing platform was designed for tactical compute resources. Work began on a multipath transport protocol designed to exploit multiple heterogeneous wireless channels.
In Thrust 3, a dual-function radio-radar platform was developed that pushed the limits of the sensing resolution and communication speed. Work progressed on the design and implementation of a self-reconfigurable dynamic mmWave backhaul. Work also progressed on harnessing full-duplex radio nodes for secure communications and developing continuous encryption and secret key generation for such radios. Finally, new algorithms were developed and investigated for over-the-air clustered federated learning and sparsified secure aggregation for federated learning.
For Thrust 4, further development and experiments were completed on the design of new method to boost TCP performance of critical applications under resource duress. Further investigations were completed regarding the impact on TCP during link switching between RF and millimeter wave links. Finally, security analyses and algorithm design were performed to develop robust ML schemes for wireless communication, and also to develop adaptive resource allocation for wireless networks that are robust to adversarial attacks.
Year 3 Accomplishments
In Thrust 1, techniques were developed for client selection for efficient federated learning, based on contextual information about data and network. Preliminary results were obtained on transformer architectures for federated/distributed learning and modular updates for single devices. Techniques were developed and evaluated to deal with heterogeneity in distributed learning. And, core algorithms were advanced for verifying robust networking behavior of application code when network conditions are varying.
Within Thrust 2, techniques were developed for multipath transport for heterogeneous network paths, addressing interactions between Mmwave links & higher-layer protocols, scheduling, congestion control, and FEC. Also, further progress was made on developing scalable and secure data driven resource allocation, leveraging reinforcement learning and graph neural networks, with new approaches for improving scalability and reducing the action space.
In Thrust 3, fundamental and useful insights were obtained into: degrees of freedoms of wireless networks using collaborative pilots; secret-key capacity based on channel probing over MIMO channels with or without reciprocity; connections between wiretap channel (WTC) theory and secret-key generation (SKG) theory. Discovery of a unification of WTC and SKG, called “secret-message transmission by echoing encrypted probes – STEEP”, which promises to have broad applications.
Additionally, the first of scalable mechanisms for secure multi-party decentralized learning tasks with formal information-theoretic guarantees were demonstrated, achieving linear communication complexity for logistic, linear regression tasks, and polynomial neural networks. Also, the federated learning client scheduling mechanisms developed in Thrust 1 were applied to physical layer resource allocation, for speeding up power allocation for massive MIMO systems. Finally, ahybrid simulation framework was created for bridging the simulation-to-reality gap in AI-driven dynamic mmWave mesh networks.
For Thrust 4, C2Store was developed, a framework that compiles information about C2 servers to provide ready information for network defense. Also, preliminary work was performed on how access control vulnerabilities in wireless meshes can lead to privilege escalation. And further techniques were developed to demonstrate adversarial machine learning examples against wireless communications.
Year 4 Accomplishments
Our work within Thrust 1 in Year 4 yielded advances in multiple areas. We developed PLUTO, a novel technique to ease the challenges of deploying large transformer models on edge devices with limited computational resources. We developed a novel sparsification method for federated learning that adapts to varying bandwidth allocations across clients. We developed an online algorithm to solve a quadratic time varying optimization problem, a challenging problem due to dependencies on unknown, dynamically evolving parameters. Finally, we completed a project on a core scalable static analysis for networking-related JavaScript code and initiated a new project on using the analysis to discover networking-related bugs in software.
Within Thrust 2, we continued developing improved multi-path transport protocols for heterogeneous wireless channels, aiming to provide efficient, resilient and fair transport protocol design for tactical environments, embodied in our work on MPQUIC. We also continued work on using Graph Neural Networks (GNNs) to capture network-wide spatial relationships and a reinforcement learning regime to enable agile data-driven decision making in the absence of supervised data. We pursued a specific problem, Service Function Chain (SFC) placement because its structure can map to other common problems in tactical networks such as multi-hop routing. We made significant advances in scaling up our solutions in this space.
For Thrust 3, we continued to build upon our research outcome in the prior years. In particular, we developed fundamentally new understandings and superior approaches for physical layer security. We designed and verified a novel federated learning approach for massive MIMO power allocation, and further introduced a new coding theoretic approach for secure computational offloading. In addition, we developed a generative agent framework for explainable and autonomous protocol design, with applications in heterogeneous wireless networks.
For Thrust 4, we made significant progress with regards to our work on wireless and IoT security. We had a paper accepted to ACM CCS 2024 on the work on wireless mesh vulnerability discovery. We have had significant work on firewall robustness and active discovery of command and control servers which we plan to submit in the near future. Prior work on reliable/robust link switching to allow TCP to exploit the available bandwidth properly when there is a switch to RF from a mmWave link and vice versa was completed and we have a new paper in ACM MobiCom 2024. There has been significant progress on understanding the impact of adversarial examples on wireless communications.